Basic Pentesting (Try Hack Me)
Hey Hackers, Today’s article will be a Writeup on Basic Pentesting Room on TryHackme. This Room is Free and Anyone can join. Plus, This Room is amazing if you want to get your hands dirty for the first time in the field of Hacking. So lets Get Started

According to the room, it is described as where the hacker will practice their skills in web and privilige escalation. So let’s get Hacking :)
TASK 1: Deploy The machine and connect to our network
After Deploying the machine, The room will assign you an IP address to connect on. You also would require to have openvpn connection in order to connect to the server

TASK 2: Find the services exposed by the machine
After we have been assigned an IP address, let run nmap in order to find the network services it is running and what OS it is. I typically use the following nmap script
nmap -A -T5 --script vuln 10.10.89.26 -vv


From the First Screenshot, we saw the following ports were opened: -
- 22
- 80
- 8080
- 139
- 445
TASK 3: What is the name of the hidden directory on the web-server?
Looking at the nmap result, port 80 seems to be open.Opening the IP address in the browser, we see that the website is under maintenance. Nothing interesting here.

Lets directory brute-force the website to see what directories it consists of i.e. in order to find interesting files and folders.
python3 ~/tools/dirsearch/dirsearch.py -u http://10.10.89.26/ -e html,js,php,aspx,asp,txt,ini,db

From the screenshot above, we found an interesting folder called development. Congratulations you found the hidden directory. Inside the development folder, there are two files hosted in the directory. They are: -
- dev.txt
- j.txt



By reading the dev.txt and j.txt file. We can assume the following information that would help us exploiting this machine. That is: -
- there are two users j and k
- samba is configured
- J has a weak password policy
Now lets enumerate samba by running the following script
enum4linux -a 10.10.89.26
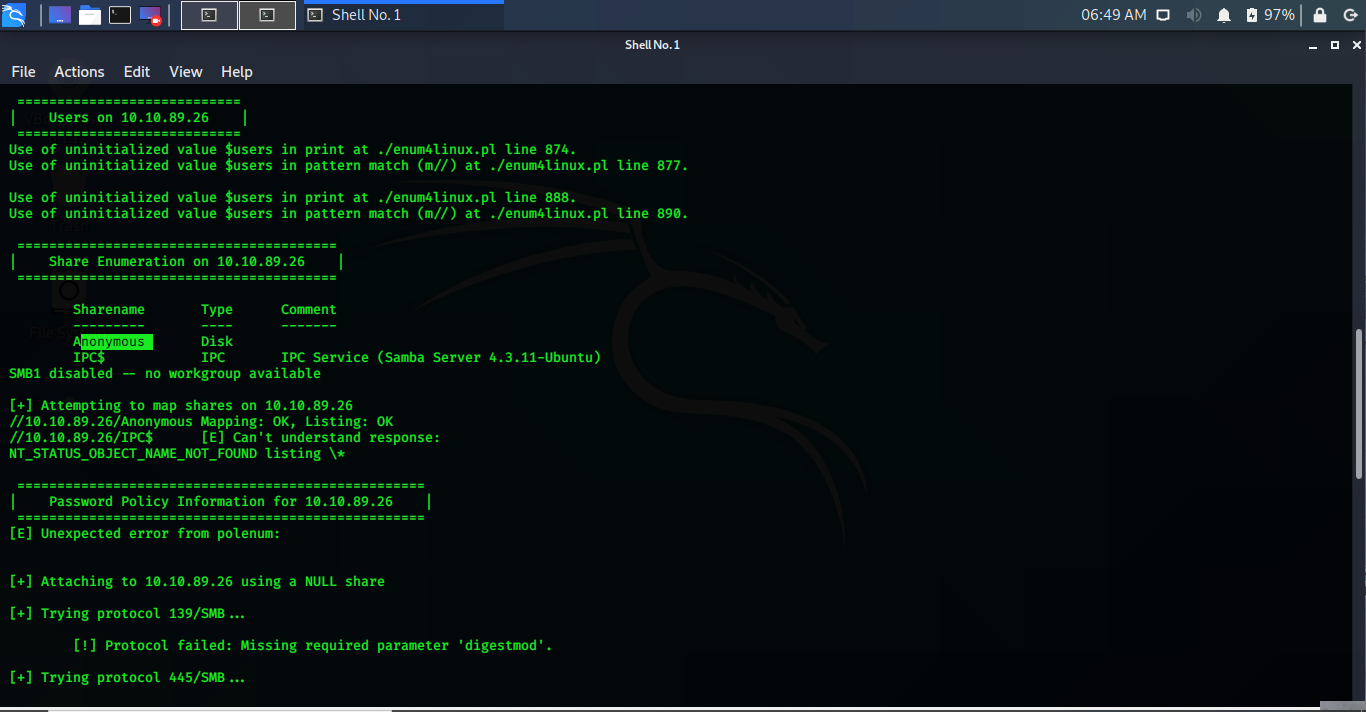
Looking at the screenshot, we can safely enter the samba shares with the default username anonymous. The command for entering into smb shares is
smbclient //10.10.89.26/anonymous

Hmmmm…There is an interesting file called staff hosted. Lets download it into our local machine and see what it consists of. In order to download the file, we used the following command
smbget -R smb://10.10.89.26/anonymous

Lets fetch the contents of the file and see what’s inside. We used the following command to read the data of the file
cat staff.txt

TASK 4: User brute-forcing to find the username & password
By reading the staff.txt file, we found the two usernames kay and Jan. From our task 3, we did know that jan has a weak password policy. Lets brute-force his account first
hydra -t4 -l jan -P /usr/share/wordlists/rockyou.txt 10.10.89.26 ssh

TASK 5 & 6: What is the username and password?
From the screenshot above, we found the password for jan. We can now use his credentials in order to enter his account. Lets fill the answers of each task

TASK 7: What service do you use to access the server(answer in abbreviation in all caps)?
Lets use his password in order to connect using ssh since port 22 is open. The command for enter through ssh is
ssh jan@10.10.89.26
As you can from the screenshot we have successfully entered into jan account


TASK 8: Enumerate the machine to find any vectors for privilege escalation
After we have successfully logged into the the jan account. We will enumerate and find what files it has or any possible vectors for privilige escalation.

From the screenshot above, we found .ssh file with access to a user called kay. It also shows that kay is the root user (Task 9 Answer)
TASK 9: What is the name of the other user?

TASK 10: If you found another user, what can you do with it?
Since we know that the other user’s name is kay and has root priviliges plus there is also an ssh file of possibility containg ssh keys. Lets see what does the file contain by using the ls -al command

TASK 11: What is the final password you obtained?
From the screenshot in Task 10, we can see that it contains the ssh-key for kay. In order to crack the key we need to copy it into our local machine.

As you can from the screenshot, we copied the key into our local machine. Now a little bit of googling, we found that in order to crack the key, one must convert the key into a hash for in order to crack it using dictionary attack. We will be using ssh2john for converting the key into a hash. The command is
python /usr/share/john/ssh2john.py id_rsa > sshkeyhash.txt

Using the cat command we can see the contents of the file has been converted into a hash.
Now in order to crack the key we will be using John the ripper tool with our favourite wordlist i.e. ofcourse rockyou.txt :p. The command for running John the ripper is
john --wordlist=/usr/share/wordlist/rockyou.txt sshkeyhash.txt

After waiting for a while, we successfully cracked the password for kay :D.
Changing to kay user
The command that will be used in order for to change to kay is
ssh -i id_rsa kay
where id_rsa is the original ssh-key and kay is the user. After entering the password i.e. beeswax. We are successfully logged in as kay:)

Navigate the files using ls command and you will find the flag with its contents

Congrats!You have completed the lab.:) However, this is not the end of it, try escalating its priviliges on your own and you will find a bonus flag with it :D